Scenario: Case involves a Full File System extraction of an iPhone, acquired by law enforcement, that was turned over in discovery with a Cellebrite Reader Report and Call Detail Records […]
cyberagents
When you have a good expert
Cyber Agents has assisted in hundreds of military trials over the last 20 years. Sometimes it’s not necessary to take a case all the way to trial. We were contacted […]
Corporate Fraud by an IT professional
Over the last 20+ years Cyber Agents has assisted in hundreds of cases some of which involve employee espionage. Today we’ll discuss a particular case where an employee was using […]
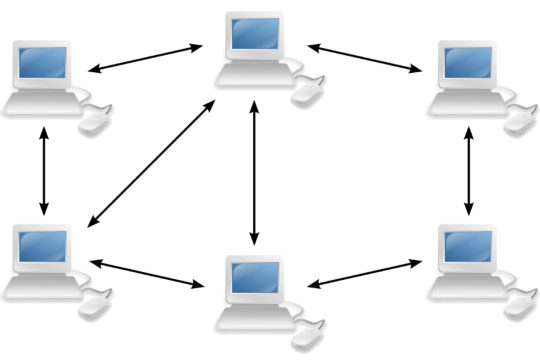
Peer-to-Peer Networks
Criminal cases in the field of digital forensics often bear morally-defunct charges, such as child pornography (CP) or child sexual exploitation (CSE). This type of content can be difficult for […]
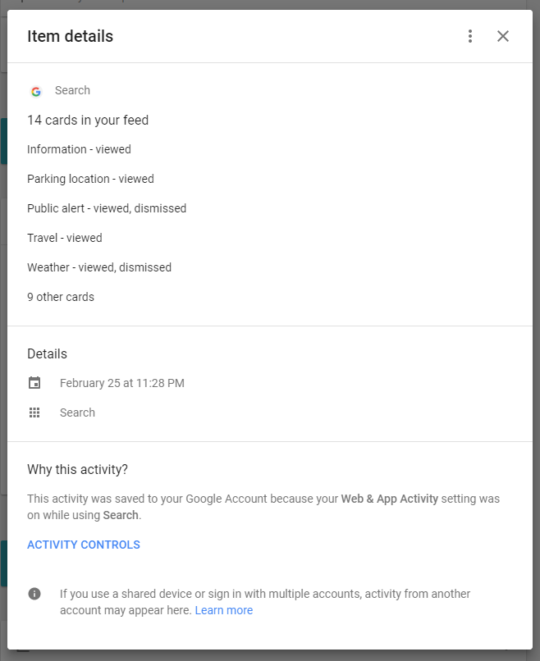
Google Location Data (Part 2)
By Matt Considine In the previous post, I discussed the ability to locate someone’s phone via their Google account location data. However, it takes more than just that data […]
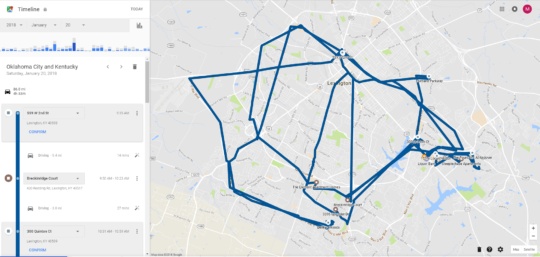
Google Location Data (Part 1)
By Matt Considine At Cyber Agents, Inc., we often find ourselves tasked with determining a client’s location on a specific day and at a specific time. Fortunately, there are […]
Snapchat Artifacts
Snapchat is an image messaging application whose biggest feature is that messages received are automatically removed after being viewed. Our goal was to figure out if any of those messages, […]
Android MMS Message Recovery
Sent messages on an Android phone may no longer be present in the MMSSMS database due to various reasons, including their having been manually deleted. Our goal was to come […]
FrostWire Artifacts
FrostWire is a popular peer to peer (P2P) file sharing service. It is a fork of LimeWire (which was shut down after losing a legal battle with the music industry) […]
Forensics Law
Yahoo Ordered to Show How It Recovered ‘Deleted’ Emails