Criminal cases in the field of digital forensics often bear morally-defunct charges, such as child pornography (CP) or child sexual exploitation (CSE). This type of content can be difficult for examiners – particularly the inexperienced. We are no stranger to these cases at Cyber Agents, as they often manifest as cyber crimes. But, how does law enforcement (LE) monitor for such crimes? How are these cases processed? How does this relate to digital forensic examiners (DFE’s)?
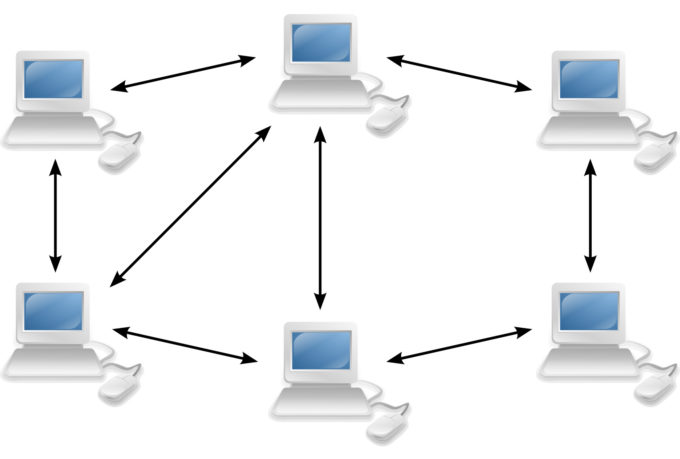
One of the most common ways we’ve seen LE track down potential predators is through the use of torrent-tracking software and passive peer-to-peer (P2P) network monitoring. BitTorrent and P2P networks are a great way of sharing massive amounts of data. So long as the files a user is looking for are available on the network, s/he will be able to download small fragments of it from multiple sources (on certain networks); this optimizes traffic across the network and allows people to download and upload several gigabytes (GB) in a small window. P2P networks rely on multiple people offering the same files for optimization, so when a user installs the client application the default settings will often be set so that a completed download will automatically start sharing to other users looking to download those files.
To fully understand how LE investigates CP and CSE distribution, it is necessary to understand how these different networks function. To explain that, we will need to look at the functional differences between BitTorrent and Traditional P2P networks, how LE handles their investigations of users on these networks, and how LE generally pursues suspects after they are identified.
BitTorrent
BitTorrent is a P2P network protocol that allows a user to download blocks of a file while sharing blocks that s/he has already downloaded. Each torrent has a corresponding set of instructions known as a “[dot]torrent” file. Users download that set of instructions and feed them into their torrent client, or application. Users are then connected to trackers either on the DHT (distributed hash table) or hard coded into the torrent file, that advertise which peers have which blocks of a torrent available. Each peer connects to one or more peers on the network and downloads some of the available blocks from multiple seeding peers.
It is important to note that most Torrent clients do not offer the [dot]torrent file themselves. In order to obtain one, you must find a [dot]torrent repository and search. Some common repositories are “The Pirate Bay”, “Kickass Torrents”, “Demonoid”, “Torrentz”, and “ISOHunt”. Some common torrent clients are BitTorrent, uTorrent (MicroTorrent), Transmission, and Vuze.
LE will often use software that monitors the traffic on the network. On torrent networks, they identify known CP files by hash connect to the tracker or DHT and then connect to a single peer offering a completed download of that file within that torrent. A torrent download consists of blocks of a standard size specified when the torrent file is created. Between 16kiB and 16384kiB. Once a specific set of blocks is complete a user will have a complete copy of that file to download. A single block can contain multiple files. As soon as a block completes downloading the block is then made available, or seeded, to other downloaders, or leechers, of that same torrent. In layman’s terms they connect to a user making entire completed files available. With BitTorrent specifically, LE software will also track the peers, or the users downloading the available files, and LE will monitor when a peer finishes the file at issue and becomes a “seeder” of that file. LE possesses tools that allow them to leech files from a single seeder without offering the files themselves. This is important because LE should never share this content to other users. A leecher refers to a downloader that does not share content back to the network.
Traditional P2P Networks
Applications such as Limewire, Frostwire, EMule, and others are known as “traditional” P2P networks. They utilize concepts such as “Ultrapeers” and “leaf” to describe the structure of the network. For example searches for files within the network need a path to follow and the database of available files needs to be made available. In order for a peer to find a file, they send a search to their designated Ultrapeer (UP). That UP searches its connected peers or leafs, “x number of peers in my group have this file”. The UP then sends that search out to other UP’s who say, “x number of peers in our groups have this file, too”. With these types of networks, a file is generally not shared back to the other peers until the download has been completed. A user can alter settings within the application to allow this, but it is not a default setting for most applications. In addition, files are shared from beginning to end and in general are not split into blocks like BitTorrent.
LE Investigation
When a file is being made available on the network, the peers need a way to identify each other, so the client application will identify them by their public IP address. If the files’ hash matches that of known CP, these tools will log that IP address, which they will then do an ARIN lookup and subpoena the internet service provider (ISP) for subscriber information of that IP address at the time the files were uploaded/downloaded. After a positive response from the ISP, LE will then get a search warrant for the subscriber’s physical address. Often, this search warrant is to seize “any and all” digital storage devices at the location and will often include verbiage that states something along the lines of, “this search warrant does not prove that any specific persons at the address are the suspect.”
After a hash analysis is performed on the seized devices, LE may identify the files they’ve been looking for. We’ve seen prosecutors bring charges against people based solely on the existence of these files on a device in their home. This is NOT how you prove a case. All too often a suspect is arrested and charges brought against him before a specific user is identified. LE and the prosecutor then need to prove who was using the device, whether the user knew of the files, and of the contents of the files, and that they had intent to possess or distribute the files. This can only be done by a DFE performing an expert analysis on the devices in question.
Once complete, the DFE should issue a report, which is facts stated with supporting exhibits, and expert opinions based on those facts. The report needs to include how the suspect was identified, how the files came to exist on the device(s), if/when the files were accessed, whether the files were deleted, and which user of the device created/accessed/deleted those files. Beyond just the files themselves, it also needs to be proved that the software used to upload these files was installed and running on the device, and whether the user was intentionally using that software to download and upload CP.
In my next few posts, I will discuss specific features of, and artifacts created by, the P2P client “ShareAza”. This is one of the most common P2P clients because of its ability to search for files across different types of P2P networks: GNUtella, GNUtella2, BitTorrent, and EDonkey2000. Since it is offered for free, anyone with an internet connection can download, install, and use the application.
Distinction:
We have also seen private individuals and organizations develop and use software that identifies CP, logs the user’s IP address, and save in a database or send it to LE for investigation. It is important to test that software to prove its functionality. If a tool has not been peer-reviewed, the Defense Counsel can present a Daubert challenge that could nullify the validity of that tool. This sort of review process generally does not happen, and someone who has not been qualified as an expert just stating that “the tool does this, and the tool does that” is not proof that the tool functions as stated.